
 obile phones are a marvel of innovation and their small size is a testament to human achievement. But mobile phones as mere phones go a long way back, decades in fact. Their functionality today has hardly changed when it comes to core objectives like making and receiving calls. So how have people come to the point of treating them as accessories and status items in our increasingly superficial social system? Why are my colleagues advertising a phone brand in all their E-mails for example? Why are people without a phone (or a Facebook account for that matter) frowned upon? Must everyone be semi-detached to a phone? Is it a status symbol? Is that how it’s marketed? Wrist watches were like that sometimes, e.g. Rolex.
obile phones are a marvel of innovation and their small size is a testament to human achievement. But mobile phones as mere phones go a long way back, decades in fact. Their functionality today has hardly changed when it comes to core objectives like making and receiving calls. So how have people come to the point of treating them as accessories and status items in our increasingly superficial social system? Why are my colleagues advertising a phone brand in all their E-mails for example? Why are people without a phone (or a Facebook account for that matter) frowned upon? Must everyone be semi-detached to a phone? Is it a status symbol? Is that how it’s marketed? Wrist watches were like that sometimes, e.g. Rolex.
I personally no longer carry a mobile phone (or cellphone to Americans) for reasons that I explained a lot of times in many different places. I do, however, carry a PDA (it was even used to compose this post with a full-sized keyboard). It’s not something that I love to talk about as it is controversial and my view is an unpopular views. Usually I avoid naming the reasons in order to avoid a pointless conversation. But here is an attempt to cohesively explain some of the factors that led me to giving up mobile phones in 2003. I am unlikely to get one again as it is like an addiction in the sense that once one is purchased, it is hard to get out of the cycle, due to people expecting your number to work, the phone to always be switched on, and for you to be near a computer even when you are not. Moreover, there are strings like contracts, which give nothing other than more complications and paperwork. Getting a mobile phone is easy, but getting out/rid of it is the hard part, as I learned 8 years ago. Among the factors that cause discomfort, as mentioned earlier in other contexts, is the associated complications that resemble getting utility bills and having to challenge mistakes, set up direct debit, check billing addresses, handle repairs, etc. Another of course is the inability to distance oneself from work. People expect people with a mobile phone to be accessible anywhere, at any time. It is unreasonable given that the phone owner might not have Internet access at every moment of the day, which is crucial for some people to operate properly in a professional way. But then there are also the elephants in the room, which make people moody or confrontational when the subject is brought up. There are primarily two such elephants; the first is privacy and the second is health. Enough said, no? The industry which profits from mobile phone extravaganza funds research to deny the health implications of associated radiation, whereas almost any study not funded by those entities shows the opposite. It’s like the tobacco lobby back in the days. Please don’t attack the messengers just because the truth is not convenient. Also, do not be selective so as to fit one’s belief of choice; it’s like faith which overcomes reasoning, even confirmation bias. Regarding privacy, more people appear to be catching up with the problem, especially recently. Using triangulation it has always been possible for carriers to determine the position of the callers (geographically) and as time goes on and antennas density increases, the identification is further refined. In the past it was not as bad as before because carriers were not legally required and retain this information for the government. They are now, as friends who work for British telcos tell me with complete confidence. This is a serious step back which shows how hostile phones are becoming. This data is not there for the user, so it can mostly be used against the user. It never goes away, either. To make matters worse, even makers of the operating systems of the phone are now probing for one’s location. How can that ever be useful to the user? Marketing? To spin this attack on privacy as something positive people might say that it’s for one’s safety, in case someone gets lost/injured/abducted and becomes “missing”. In practice, however, It is rarely the case that the phone becomes a saviour unless a call is being made. So the privacy part of it (location recording with a long trail of history) is an entirely invalid point. Why retention?
The subject of privacy is better understood by those whose activities might be seen as subversive by some who themselves subvert society. The vigilant ones amongst us understand that privacy protects us from those who have too much power.
The one major circumstance where having a mobile phone would be invaluable is when trying to coordinate a meeting with someone out in town or some streets where a land line is not easily accessible. But that someone would have to be unreliable as people could arrange meetings and avoid being late long before mobile phones. Today’s generation got accustomed to the idea of using a phone to justify being late (people are still late, but they get reassurances and estimated times of arrival, which is not ideal either). If the train system was run like this, there would be considerable trouble.
The matter of fact is, a lot of people these days use their mobile phones for purposes they were not designed for, e.g. loud conversations about what’s available for lunch. It becomes an attention-seeking apparatus and less of a tool of necessity. People give away phones to workers or family in order for them to be contacted rather than in order for them to make contact and if they cannot be reached there is an unsubstantiated fear and paranoia. Rather than quell and suppress uncertainty (when someone can or cannot be reached) it just causes more anxiety.
Do you still carry a mobile phone? And if so, have you tried carrying none for a whole month as an experiment? It would probably not be an ideal experiment due to the tie-up or addiction mentioned at the start of this post. It’s a cyclic trap, more so than addictive computer games. Social interaction manifests peer pressure. The truth is, even without a mobile phone people can do all the same things; there are substitutes for everything and nothing ever rings to interrupt an epiphany.







 Filed under:
Filed under: 

 obile phones are a marvel of innovation and their small size is a testament to human achievement. But mobile phones as mere phones go a long way back, decades in fact. Their functionality today has hardly changed when it comes to core objectives like making and receiving calls. So how have people come to the point of treating them as accessories and status items in our increasingly superficial social system? Why are my colleagues advertising a phone brand in all their E-mails for example? Why are people without a phone (or a Facebook account for that matter) frowned upon? Must everyone be semi-detached to a phone? Is it a status symbol? Is that how it’s marketed? Wrist watches were like that sometimes, e.g. Rolex.
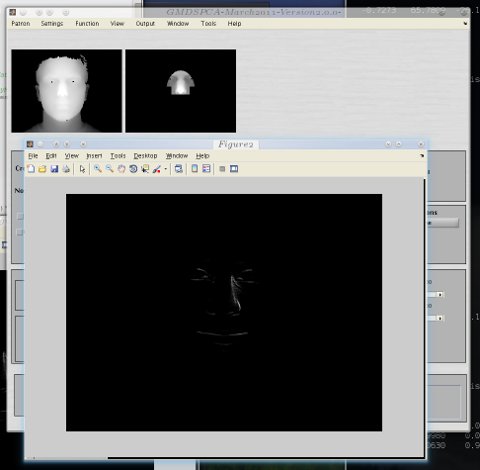
obile phones are a marvel of innovation and their small size is a testament to human achievement. But mobile phones as mere phones go a long way back, decades in fact. Their functionality today has hardly changed when it comes to core objectives like making and receiving calls. So how have people come to the point of treating them as accessories and status items in our increasingly superficial social system? Why are my colleagues advertising a phone brand in all their E-mails for example? Why are people without a phone (or a Facebook account for that matter) frowned upon? Must everyone be semi-detached to a phone? Is it a status symbol? Is that how it’s marketed? Wrist watches were like that sometimes, e.g. Rolex. recently needed to gather 3-D data of different people’s faces, in order to perform experiments on these and test new algorithms that I had developed. The problem was, without some metadata regarding expressions, how might I find correct pairs suiting a particular criterion/ia? Two universities that I contacted had some data of this kind, but they were unwilling to share it (Open Data principles betrayed). So I had to do it myself using a dataset I mentioned here before [
recently needed to gather 3-D data of different people’s faces, in order to perform experiments on these and test new algorithms that I had developed. The problem was, without some metadata regarding expressions, how might I find correct pairs suiting a particular criterion/ia? Two universities that I contacted had some data of this kind, but they were unwilling to share it (Open Data principles betrayed). So I had to do it myself using a dataset I mentioned here before [

 “Sei La” by Erika Machado (SXSW 2010 Showcasing Artists) and
“Sei La” by Erika Machado (SXSW 2010 Showcasing Artists) and