How many years will those lies and SPAM carry on for? There’s no “opt out”.
 EVERAL years ago I wrote about the spamming I had been receiving about spy meters. I must have been nagged about it about 100 times already. It’s very time consuming at this rate and frequency. They even phone us sometimes to nag us about it.
EVERAL years ago I wrote about the spamming I had been receiving about spy meters. I must have been nagged about it about 100 times already. It’s very time consuming at this rate and frequency. They even phone us sometimes to nag us about it.
By their own admission, more than a third of their clients do not want spy meters. So we’re not some tiny minority or a ‘fringe’.
Anyway, in recent days they kept spamming me some more and even a day after they told me it would stop they carried on as usual. See below.
E.ON Next wrote on 19/02/2024 15:20:
> Hi Roy Schestowitz,????
>
> Thank you for your email.
>
> I am Shameemah Your Energy Specialist that will be assisting you today.
>
> We have reviewed your account and due to what you have mentioned we have updated your email address on the account to the one you have provided us with [...].
>
> We have done a few health checks on the account and we can see that we do require up to date meter readings this is to avoid your readings being estimated and we need regular readings to bill your account accurately to that you won’t be under or over charged as this could lead to future debt onto your account and we do not want that.
>
> To avoid this I know the days can get busy and can forget we do see that you are eligible to have a free smart meter installed its not complicated basically like the normal meter, however with a smart meter we will be getting readings automatically without you have to send manual readings regularly, your account will be billed regularly and accurately, you will also receive a free in home display a monitor which you will be able to monitor your usage.
>
> Before I can book your appointment there are just a few questions I need you to answer so I can ensure the appointment is correct and the engineer has all the information they’re going to need on the day.
I already told you, REPEATEDLY, to stop spamming me about this.
You agreed but didn’t keep the promise.
You’re still doing this.
Please STOP.
Ross from E.ON Next wrote on 19/02/2024 18:42:
> Hello Roy.
>
> I will remove correspondence about this from your account.
Nonsense. The SPAM continues just less than 24 hours later.
I will relay to you the SPAM.
At this stage I might just terminate the contract with you and report the SPAM, or unsolicited mail.
Notice the date on this email
——– Forwarded Message ——–
Subject: smart meters
Date: Tue, 20 Feb 2024 11:30:47 +0000
From: Shameemah from E.ON Next <shameemah.bowers@eon-next-cabac46b5ea2.intercom-mail.com>
Hi Roy Schestowitz,????
Thank you for your email.
I am Shameemah Your Energy Specialist that will be assisting you today.
We have reviewed your account and due to what you have mentioned we have updated your email address on the account to the one you have provided us with ….
[then pushing for spy meters again]
 N the morning (around 10AM) ONS published these latest figures of public interest, this time with Week 6 mortalities in England and Wales (not Scotland). It’s about 1,000 higher than it was before the pandemic (for this one week alone, only in England and Wales).
N the morning (around 10AM) ONS published these latest figures of public interest, this time with Week 6 mortalities in England and Wales (not Scotland). It’s about 1,000 higher than it was before the pandemic (for this one week alone, only in England and Wales).





 Filed under:
Filed under: 

 EVERAL years ago I wrote about the spamming I had been receiving about spy meters. I must have been nagged about it about 100 times already. It’s very time consuming at this rate and frequency. They even phone us sometimes to nag us about it.
EVERAL years ago I wrote about the spamming I had been receiving about spy meters. I must have been nagged about it about 100 times already. It’s very time consuming at this rate and frequency. They even phone us sometimes to nag us about it.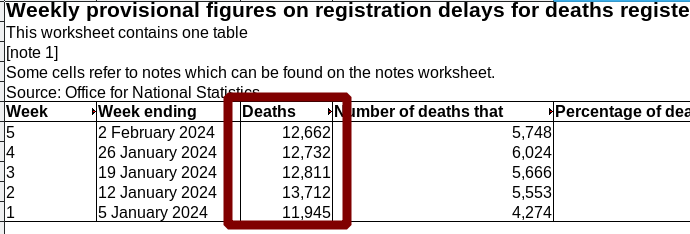
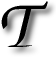 he new numbers from ONS are
he new numbers from ONS are