Cost-effective Computers

 cedemic institutes seek to provide a large number of workstations to their students. The more workstations, the more of computer-based education fits into the school’s curriculum. An observation can be made which says that schools buy the wrong computers. Licences for the software they run, despite the bulk discounts, can cost as much as the computer itself, if not exceed that cost. When accommodating a computer cluster and paying over $1000 per Windows-based machine, the number of available computers will inevitable drop. As Linspire.com shows, each student in Indiana will soon have his/her own Linux box at school. This is particularly important where kids do not have a computer at home. Will more schools follow suit? This certainly happens in Manchester as well, albeit rather slowly.
cedemic institutes seek to provide a large number of workstations to their students. The more workstations, the more of computer-based education fits into the school’s curriculum. An observation can be made which says that schools buy the wrong computers. Licences for the software they run, despite the bulk discounts, can cost as much as the computer itself, if not exceed that cost. When accommodating a computer cluster and paying over $1000 per Windows-based machine, the number of available computers will inevitable drop. As Linspire.com shows, each student in Indiana will soon have his/her own Linux box at school. This is particularly important where kids do not have a computer at home. Will more schools follow suit? This certainly happens in Manchester as well, albeit rather slowly.

RedHat Linux
As hardware costs drop, it is gets harder to defend the purchasing of commercial software. The price of development does not not necessarily rise because of offshoring, but the availability of richer Open Source software goes up owing to the Internet, killing commercial equivalents in the process. This, in fact is one of the reasons for the success of Windows 95. Back in the days, plenty of software was bundled while getting new applications remained a time-consuming task in the absence of rapid access to the Net.






 Filed under:
Filed under: 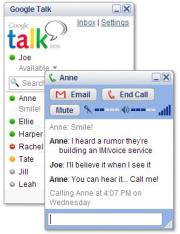


 My seriousness when it comes to backup
My seriousness when it comes to backup 
 everal companies including Google have devised mechanisms so as to avoid becoming the hosts to spammers. It is broadly agreed that spam blogs (also referred to as “splogs”) and spam-generating E-mail accounts can easily damage the reputation of the ISP or the on-line service which provides the bandwidth. Consequently, Google have reacted to
everal companies including Google have devised mechanisms so as to avoid becoming the hosts to spammers. It is broadly agreed that spam blogs (also referred to as “splogs”) and spam-generating E-mail accounts can easily damage the reputation of the ISP or the on-line service which provides the bandwidth. Consequently, Google have reacted to 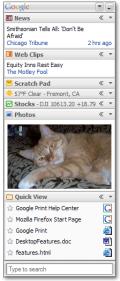 Only months after the release of
Only months after the release of