
 ave you ever wondered how to extend the lifetime of your battery? Or perhaps reduce the electricity consumption at your home? Shutting off the machine is not the only option, as the remainder of this item explains with particular emphasis on state-preserving energy-saving schemes.
ave you ever wondered how to extend the lifetime of your battery? Or perhaps reduce the electricity consumption at your home? Shutting off the machine is not the only option, as the remainder of this item explains with particular emphasis on state-preserving energy-saving schemes.
Most idle computers enter the screen saver mode after a certain, pre-defined period of time (some readers will prefer “screensaver” as one word, like “screenshot”) . Screen savers are by large the default and most common scheme, but it does not preserve much energy. As a matter of fact, with some of today’s screen savers, even more power is consumed when they are run. Resource-hogging screen savers, which make use of hardware acceleration, are among the most poplar too. Call it office vanity if you like, but that is an issue for another day.
At the end of the previous decade we began to see monitors that were more energy-efficient and environmentally-friendly. They supported auto-shutoff schemes and consumed less electricity than predecessors even though their size grew. With today’s TFT screens, things continue to improve.
 Laptop sales in the States exceeded sales of desktop last year, so they are definitely here to stay (and expand). Due to the nature of laptops and their pricy batteries, energy saving in laptops is worth greater attention.
Laptop sales in the States exceeded sales of desktop last year, so they are definitely here to stay (and expand). Due to the nature of laptops and their pricy batteries, energy saving in laptops is worth greater attention.
Stand-by mode is a popular energy saving scheme, which results in an idle system state, but the user would be killing off expensive batteries by opting for stand-by. The big pro is the quick wake-up time. You will frequently be advised not to use stand-by mode unless you leave your laptop connected to the socket or return shortly. With stand-by as standard, you will opt for data retention on RAM, which uses up power. Come back after a few days, and your battery might be flat. Sources I can recall claim that a battery in the body of the laptop never benefits, even if the laptop is bound to a source of electricity. Then fluctuation between 90% and 100% battery capacity also appears to be unhealthy.
As opposed to stand-by, another scheme exists which is called hibernation. Hibernation will mirror the memory and place it on non-volatile magnetic storage device — the hard drive. Maintenance of laptop batteries sums up as a whole ‘bible’ on its own and will not be discussed further for the time being. Overall, battery drainage depends on memory, laptop’s architecture, O/S and battery’s capacity (or type). The user can experiment to determine the battery’s lifetime. However, such a curious user often assumes that the battery meter shows depletion linearly, which is rare.
Also worth mentioning are mechanisms by which hard-drive rotation stops whenever operations involving the disk appear unnecessary. Moreover, there are schemes such as the lowering brightness (laptops and PDA‘s in particular), which is also a phase that is invoked automatically. When the user presses no key (or taps the screen) for some period of time, brightness (or backlight) is significantly lowered.
Lower consumption of power in desktop computer does not just cut the bill, but also has positive effects on our environment. This argument is boosted particularly today as we hear about global warming and its impact in Siberia. In terms of security, switching off of our computers has often been advised to Windows users, who are exposed to more attacking attempts (last critical patch two days ago). Likewise, in large computer clusters, switching off is an issue that extends beyond energy savings. It prevents accumulation of zombies across computer clusters worldwide.

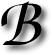 ack when I was in school, some friends of mine were addicted to on-line role-playing games (RPG) such as Ultima (interview with its creator just Slashdotted). One of them would spend his entire life (not literally as he was in school too) playing D&D-themed games, attending his friends’ on-line weddings and grabbing screenshots. The Diablo extravaganza was heated up too at the time, but it goes back to the age of 14 or 15.
ack when I was in school, some friends of mine were addicted to on-line role-playing games (RPG) such as Ultima (interview with its creator just Slashdotted). One of them would spend his entire life (not literally as he was in school too) playing D&D-themed games, attending his friends’ on-line weddings and grabbing screenshots. The Diablo extravaganza was heated up too at the time, but it goes back to the age of 14 or 15.





 Filed under:
Filed under:  A heavily-discussed topic in this quiet August is Mac OS X piracy. Yet more sets of instructions flow in, which explain about (at least) 3 different ways of installing Mac OS X on non-Apple workstations. To give a snippet of
A heavily-discussed topic in this quiet August is Mac OS X piracy. Yet more sets of instructions flow in, which explain about (at least) 3 different ways of installing Mac OS X on non-Apple workstations. To give a snippet of 
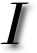 definitely enjoy running my Web log, but
definitely enjoy running my Web log, but  overnmental offices and agencies are expected, more than any other body, to cater for a large variety of cultures. This item is not a political one, but it refers to governments which unknowingnly support a commercial monopoly, which happens to be a majority. The benefit to governments taking this stance is scarce or inexistent. At the end of the day, cash only flows towards the folks at Washington state.
overnmental offices and agencies are expected, more than any other body, to cater for a large variety of cultures. This item is not a political one, but it refers to governments which unknowingnly support a commercial monopoly, which happens to be a majority. The benefit to governments taking this stance is scarce or inexistent. At the end of the day, cash only flows towards the folks at Washington state.
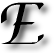 arly this morning I made a bold move; it was bold for me, at least. I decided to make both partitions on my hard-drive adhere to the Reiser filesystem (FS), overwriting an unused Windows 2000 (NTFS) partition, which was rarely ever accessed. At times it was exploited as a storage area, yet no more than once month, which made it a complete waste of space.
arly this morning I made a bold move; it was bold for me, at least. I decided to make both partitions on my hard-drive adhere to the Reiser filesystem (FS), overwriting an unused Windows 2000 (NTFS) partition, which was rarely ever accessed. At times it was exploited as a storage area, yet no more than once month, which made it a complete waste of space.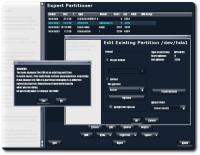




 ave you ever wondered how to extend the lifetime of your battery? Or perhaps reduce the electricity consumption at your home? Shutting off the machine is not the only option, as the remainder of this item explains with particular emphasis on state-preserving energy-saving schemes.
ave you ever wondered how to extend the lifetime of your battery? Or perhaps reduce the electricity consumption at your home? Shutting off the machine is not the only option, as the remainder of this item explains with particular emphasis on state-preserving energy-saving schemes. Laptop sales in the States
Laptop sales in the States