
Shut your ears, stop the radiation and avoid the fumes
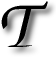 O this date, I loathe the prevalence of high-intensity antennas, particularly those that serve mobile communication. These are often installed on the top of roofs of businesses, which in turn get paid (bribed) to tolerate consequent inconveniences. It was only last month that I came to discover one such controversy. This happened at a hotel I used to go to, where demonstrations by local residents were sparked by a decision to install monstrous antennas.
O this date, I loathe the prevalence of high-intensity antennas, particularly those that serve mobile communication. These are often installed on the top of roofs of businesses, which in turn get paid (bribed) to tolerate consequent inconveniences. It was only last month that I came to discover one such controversy. This happened at a hotel I used to go to, where demonstrations by local residents were sparked by a decision to install monstrous antennas.
I still refuse to embrace telephony (alluded to in this previous essay) unless it is vital. I am aware of the ‘radiative implications’ of cellular phones, especially when they are active, i.e. on call. Vis-a-vis, my father encouraged my older sister to always use headphones and a microphone with her cellular phone, if not limit its use altogether. The issue of radiation lingers on and exacerbates as time goes. The reason: wireless communication rises owing to customer demand and bandwidth greed.
To digress, then comes the issue of wireless Internet networking, which I have always been wondering about with health complications/implications in mind. Whether commonplace Wireless or even Bluetooth, such radio frequencies of strong magnitude increase the risk level or rate of tumour growth and development. Turning over to some recent news, you can finally find a University where wireless access has been limited due to health concerns.
Criticism of wireless network is somewhat of a taboo, still. You cannot comfortably point this out among your surrounding colleagues and friends. The crushing majority does not care and does not want to know about the long-term consequences, which are yet to affect the young(er) generation most prominently.
While on the subject of self-damaging habits amongst society, choice of headphones should be yet another important matter. Many choose in-ear headphone and listen to loud music. Some of the local clubs would leave my ears ringing for 2 days afterwards, so no doubt damage is being done.
Lastly, my last health concern is related to smoking. Fortunately here in Britain, nightclubs and pubs were very recently requested to inherit and embrace the “No Smoking” policy, thereby joining other venues like the workplaces. Surely enough, some of us could abstain from going to smoky places, but what about the staff — those who do not necessarily smoke? The smoke-free workplace arguments collide. Some employees at the pubs, such as bartenders, may spend dozens of hours per week passively exposed to constant inhalation of damaging smoke. It clogs up the lungs, ruins the voice, and makes the clothes reek. That is not a matter of choice, but a way of making ends meet.
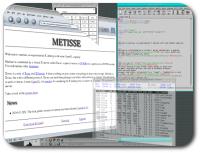
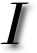 have just had a rare chance to become part of an exciting experiment. It took place at the The Manchester Visualisation Centre, which is near my office. This involved a new method for interaction with visual data.
have just had a rare chance to become part of an exciting experiment. It took place at the The Manchester Visualisation Centre, which is near my office. This involved a new method for interaction with visual data.





 Filed under:
Filed under: 
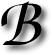 ILL Gates comes from a
ILL Gates comes from a 

 O this date, I loathe the prevalence of high-intensity antennas, particularly those that serve mobile communication. These are often installed on the top of roofs of businesses, which in turn get paid (bribed) to tolerate consequent inconveniences. It was only last month that I came to discover one such controversy. This happened at a hotel I used to go to, where demonstrations by local residents were sparked by a decision to install monstrous antennas.
O this date, I loathe the prevalence of high-intensity antennas, particularly those that serve mobile communication. These are often installed on the top of roofs of businesses, which in turn get paid (bribed) to tolerate consequent inconveniences. It was only last month that I came to discover one such controversy. This happened at a hotel I used to go to, where demonstrations by local residents were sparked by a decision to install monstrous antennas.
 NE powerful technique to avoiding spam are
NE powerful technique to avoiding spam are 
 ROPOSALS have become Europe’s on-paper solution to America’s economic strength. Another proposal
ROPOSALS have become Europe’s on-paper solution to America’s economic strength. Another proposal 