Sunday, March 5th, 2006, 11:40 am
Directory Listing as a Vulnerability?
The WordPress dashboard, as secure as ever
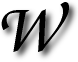 ORDPRESS continues to be a secure and robust piece of Web-based software. Rumours, however, sometimes stand in its way. Below is one example among several, which have been ‘severe’ enough to trigger high-profile advisories. All the hoi polloi was, needless to mention, in vain.
ORDPRESS continues to be a secure and robust piece of Web-based software. Rumours, however, sometimes stand in its way. Below is one example among several, which have been ‘severe’ enough to trigger high-profile advisories. All the hoi polloi was, needless to mention, in vain.
It sometimes appears as though such rants are desperate attempt to stir up a hornet’s nest. WordPress has become a prime target due to its popularity and existence as Web-based software, making it more exposed to the factor of traffic en masse. Google have become a target for rumours, the reasons being very similar.
Apart from minor wishlist items or bugs, such as one that I recently filed, there are more pressing issues that need resolving and require open clarifications from the community. More latterly, a concern was raised over the visibility of WordPress plug-ins to all site visitors. My opinion on the matter was phrased therein (see full thread for context).
Directory listing, which in turn exposes plug-in names, is never being linked to. Thus, it will not be indexed by search engines and flawed plug-ins will not be easily discoverable.
You could trivially scan many blogs using a script in attempts to find vulnerabilities. PHP-Nuke, Advanced Guestbook and Coppermine are notorious in that respect.
All in all, getting a list of plug-ins may be a convenient way for learning the blog’s composition. If you target a particular vulnerability (due to third-party code), it gives the hacker no advantage. That,
marke1, is why your argument and its ludicrous, overstated backing are void.






 Filed under:
Filed under: