Auction of Excel Vulnerability Intercepted by eBay

As information is offered for sale, negotiation
by telephone can seal such transactions
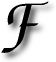 ROM ZDNet comes as item that speaks of yet another odd item ‘on sale’. The article states: “An online auction of a “brand new vulnerability” in Microsoft Excel had reached about $60 when eBay pulled the item late Thursday. A seller using the name “fearwall” started the auction Wednesday evening at 1 cent. It was up to $56 on Thursday afternoon with 21 bids placed, and eBay quashed the auction soon after that.”
ROM ZDNet comes as item that speaks of yet another odd item ‘on sale’. The article states: “An online auction of a “brand new vulnerability” in Microsoft Excel had reached about $60 when eBay pulled the item late Thursday. A seller using the name “fearwall” started the auction Wednesday evening at 1 cent. It was up to $56 on Thursday afternoon with 21 bids placed, and eBay quashed the auction soon after that.”
Other strange items which I can recall eBay boasting: chewing gums that have been sput out by celebrities, fake love letters, and potato chips.






 Filed under:
Filed under: 

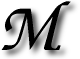 AKERS of Windows are
AKERS of Windows are