
Summary: In Sirius ‘Open Source’, neither Open Source nor security got taken seriously enough. Siriusly! And one cannot point this out to managers as this infuriates them (it harms a false perception they’ve long cultivated).
TODAY we turn our attention to bad security practices, including poor privacy and unbridled outsourcing of Sirius. There will be numerous parts about these aspects and we’ll provide some examples in the future when dealing with proprietary software, introduced by the company itself while tearing down its very own Free software-based infrastructure (which had been put there when the company still had geeks in the office; heck, the company used to have an actual office!).
Suffice to say, patching is part of the work, including patching one’s own machine. Anything else would be irrational (like blasting people over “commuting” time) because security starts in one’s own domain. And yet, I was being told off by the company’s founder for patching my PCs while I was on shift despite the fact that there are several such machines (if one encounters an error, then one can rely on another machine) and this is about actual security.
It took me a while to find E-mail regarding this, as it dates back nearly 4 years. My redacted response below:
I have just caught up with E-mail (resting and other things since 9am).
Sorry for the delay in responding.
Roy,
I have read your shift’s handover notes where I find this from you:
“Quiet shift, so I took the time to update my whole system. Something broke nagstamon for me, briefly, but I managed to fix it. In the meantime I used the Nagios/Icinga Web interface.”
I use 3 laptops in parallel to do my job, so this was one in three and Nagios remains accessible regardless. nagstamon is an alternative to it (sound alerts) and I wanted to bring it up to date for security reasons. As I do often, to avoid breaches.
This is *absolutely unacceptable*.
If I cannot observe systems that are monitored and supported, it’s not “unacceptable”. It’s still very much necessary. But still, looking back, there are many serious (Sirius) issues that were shared in the report below (more to come in the next parts).
Acronyms Lingo
Speaking of “GDPR” or “ISO” without even grasping the meaning behind laws and regulations is “cheap talk”. Without comprehension of the issues, this boils down to ‘name-dropping’ (like “GDPR” or “ISO”). Currently, the company would gladly take technical advice from people who openly admit they don’t care about privacy. So instead Sirius falls back onto formalities and processes rather than any real grasp of the underlying issues. Sirius track record will be demonstrable based on recommendations from past clients; with or from at least two clients we might only get an alarming reminder that their systems suffered a security breach while we supported them. The clients’ names are, as usual, omitted here, but this is very well documented. There may have been more security incidents that were hidden or concealed both from clients and from Sirius staff. Considering the atmosphere of secrecy and hostility towards inquisitive staff, it seems likely more incidents occurred but weren’t reported at all (or reported very selectively).
Speaking of formalities and processes rather than actual substance, the company Sirius was pursing ISO certification only amid some issues with NHS and its highly sensitive medical data — including several incidents staff witnessed where people’s (patients’) privacy was accidentally compromised, either by Sirius or by the client (personally identifiable data divulged). To make matters worse, many times data was not being shredded like it was supposed to and the client complained. If better leadership was in place, this would not have happened, jeopardising the credibility of staff.
Account Management Practices and Data Sovereignty
With quite a lot of clients, and several can be vividly recalled, Sirius failed to remove access credentials (or accounts) for staff that had already left Sirius. ‘Low level’ staff cannot access systems at a level of user management, so this was demonstrably a ‘high level’ failure. Sometimes clients complained about such gross incompetence (if clients could even figure out who still works for Sirius; remember that Sirius misled them, as shall be noted again later) and potential security breach by former and possibly disgruntled Sirius staff, but nobody (as far as we know) was being held accountable. The aforementioned sections noted that accountability only ever works in this hypocritical and vertically-inconsistent fashion. Double standards became the new company standard, enshrined covertly but not formally. Managers never offered the courtesy of taking full responsibility. Too much pride to acknowledge mistake and lapses.
As the above shows, there are endemic problems caused by mismanagement or a lack of charismatic-yet-humble leadership (maladministration), maybe even a lack of staff that possesses ample experience managing a team of more than one person. These are very essential skills which mandate suitable recruitment. It may not be cheap, but it is vital.
Sirius has user credentials scattered all over the place, not all in OpenLDAP as done in the past (when more competent people managed the company’s infrastructure). This will, inevitably, result in epic blunders. That keeps happening. Again and again. In fact, user credentials management at Sirius has been partly outsourced to third parties — a taboo subject. No more GOsa, go USA (most data and authentication sent across the Atlantic).
The motivations seem petty, e.g. sharing accounts to save money despite clear security requirements that exist to explicitly not do this. Is ISO being treated as merely a box-ticking exercise, not followed up by any potent audits? If so, are we entitled to brag about some ISO compliance? Any time Roy attempted to bring up the subject the management became paranoid and threatening. This sort of resistance to ethical and moral objection would be strongly discouraged in companies capable of self-appraisal.
A colleague once mentioned in an E-mail that some colleagues may have needed to share an account with another person, all in the name of saving money. This kept happening for years despite such ISO requirements supposedly being fully in force. Account sharing was sometimes imperative, as individual accounts did not exist. In other words, all colleagues use the same username for some tasks; sometimes this was only belatedly addressed, partially and virtually post hoc.
Password management in the company has long been a painful affair. From non-secure connections to a lack of VPN for access to passwords the company moved to outsourcing. This was a case of “bad optics”, pragmatic issues aside. Sirius could self-host similar software that was Free and Open Source software, but the company had a mindset of outsourcing almost everything to proprietary offerings from another country. As noted separately, Roy raised alarm over this several times, noting or pointing out actual data breaches of a very large scale, but no action was subsequently taken. The assurances were empty and arguably arrogant — a refusal to listen to vigilant security experts who extensively covered those issues for decades. Asking a company itself whether it suffered a security breach and what the severity truly is like asking an American president what happened in the Oval Room.






 Filed under:
Filed under: 




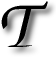 HERE IS a disturbing trend which is shared among pretty much all lawyers and other ‘legal’ professionals. I know because I checked. I also know because I saw how my friend, Pamela Jones (the paralegal behind Groklaw), got spooked by the spooks and stopped writing online after she had rejected my offer to use encryption about 8 years ago (saying it would only attract more attention). These are smart people who seem to be ignoring the threat of surveillance even when the threat is out there in the open, thanks to people like Edward Snowden. A lot of what Snowden showed had been known to me for years, but now there is undeniable truth which even the NSA’s chronic lies cannot cover up and shed uncertainty on. Ignorance is no longer a valid excuse.
HERE IS a disturbing trend which is shared among pretty much all lawyers and other ‘legal’ professionals. I know because I checked. I also know because I saw how my friend, Pamela Jones (the paralegal behind Groklaw), got spooked by the spooks and stopped writing online after she had rejected my offer to use encryption about 8 years ago (saying it would only attract more attention). These are smart people who seem to be ignoring the threat of surveillance even when the threat is out there in the open, thanks to people like Edward Snowden. A lot of what Snowden showed had been known to me for years, but now there is undeniable truth which even the NSA’s chronic lies cannot cover up and shed uncertainty on. Ignorance is no longer a valid excuse. ookies and cross-site connections help track Internet users in ways far worse than most people realise. People assume that when they visit a particular site then it is this site alone which knows about them. Moreover, they assume that they are logged off and thus offer no identifying details. In reality, things are vastly different and it is much worse when public service sites act as “traps” that jeopardise privacy. A site that I recently looked at (as part of my job) does seem to comply with some of the basic rules, but
ookies and cross-site connections help track Internet users in ways far worse than most people realise. People assume that when they visit a particular site then it is this site alone which knows about them. Moreover, they assume that they are logged off and thus offer no identifying details. In reality, things are vastly different and it is much worse when public service sites act as “traps” that jeopardise privacy. A site that I recently looked at (as part of my job) does seem to comply with some of the basic rules, but 
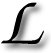 ATEX helps render for a variety of output types including posters and Web pages, not just A4 sheets. As a typesetting language it is very powerful, but for advanced functionality it requires additional packages, included in the preamble. It appears as though GIF animations are not supported in LATEX despite the fact that, if exported as Web pages for instance, the notion of animation makes sense. This is a shame really and if someone knows of a workaround, please leave a comment. I am currently writing a 400-page report which is a comprehensive summary of what I am doing and without animations it might be hard to express what is going on. For example compare the following triplet of static and dynamic (which HTML is happy with):
ATEX helps render for a variety of output types including posters and Web pages, not just A4 sheets. As a typesetting language it is very powerful, but for advanced functionality it requires additional packages, included in the preamble. It appears as though GIF animations are not supported in LATEX despite the fact that, if exported as Web pages for instance, the notion of animation makes sense. This is a shame really and if someone knows of a workaround, please leave a comment. I am currently writing a 400-page report which is a comprehensive summary of what I am doing and without animations it might be hard to express what is going on. For example compare the following triplet of static and dynamic (which HTML is happy with):




