Non-Evolving Search Engines and Operating Systems

Refuse to explore and stay a monkey forever
 oogle algorithms are very complex at present. The very core of these remains PageRank — a mechanism that often gets misused and leads to disasters (referrer spam among other link spamming techniques). For my recent zombie attacks I blame:
oogle algorithms are very complex at present. The very core of these remains PageRank — a mechanism that often gets misused and leads to disasters (referrer spam among other link spamming techniques). For my recent zombie attacks I blame:
- Google – for unintentionally leading to ‘link greed’, not understanding or anticipating streetsmarts and penetration of second- and third-world countries into the Internet
- ISP‘s – for apathetically harbouring traffic that is pure spam or targetted attacks
- Microsoft – for creating an operating system that is so easy for crooks to capture
Google’s algorithms have become like a horse that has lots of decorations upon it, but is nothing more than a brute-force horse underneath. You can take a pig, put it in a dress and take it out for dinner. But it’s still a pig in dress, not a girlfriend.
Search must Evolve. A flawed or limited principle at the heart of something is bound to fail no matter how many bits you hang atop to patch it up and improve it. This is why traditional page indexing is not a good method for approaching the problem of information extraction and discovery. Microsoft’s operating system, for instance, suffers from the very same problem where a flawed and too complex an operating system was build from ‘code spaghetti’. It was recently heard through the grapevine that Longhorn was thrown away and reverted merely to ground zero to be based on the XP-related Server 2003 code. This comes to show that weekly updates were merely patching a mordid mess. Microsoft recognise their inability to complete with Linux performance (uptime, flexibility — the a reason for Monad). Linux just took a right approach — a right paradigm if you like — all along and was therefore able to sweep along all the best programmers in the world.
Returning to Google, by relying heavily on PageRank and making ad-hoc improvements, no real innovation will be made. This is why I intimated Iuron a few days ago. It ought to turn a large pool of indexed page into actual knowledge and provide definitely answers rather than a linear scatter of related pages.
Also comes to mind are AltaVista and other antiquated search engines with very fundamental and not-so-cunning methods for scanning pages. These were very quickly relaced by backlink-based engines, i.e. link counting in 1998. No progress has been made in nearly 8 years, however. One may begin to conceive a Google killer rather than a Windows killer. The required resources, however, in particular data centres, make the (financial) entry barrier too high to initiate a substantial enough threat. Proprietaries, however, are no concrete barrier, in contrary to the case with operating systems. So, I remain optimistic and I might soon meet some professors whose expertise is the semantic Web.
With reference to the famous 3-monkey image on top (I also have one on top of my monitor), those who refuse to evolve (Ballmer) show ‘zoo symptoms’ already. I vividly recall the day when Scoble quoted Microsoft CEO, Steve Ballmer, saying that RSS has no future. This was roughly 7 months ago. Ballmer also said that Google would vanish in 5 years and promised that MSN search was bound to ‘kill’ Google. I say: live in the past, be the past.
Moving on to a different topic, the latest article with the theme of aging at Microsoft came out on the day when I first composed this item: Pity poor Microsoft’s midlife crisis. Another recent article I have just been informed of is At 30, Microsoft Grapples With Growing Up.
Recommended reading:
- Insightful Microsoft Hatred FAQ – snippet below
Q: What about all the people in the corporate environments who are forced to use MS products and aren’t allowed the option/choice to use Mac/Linux/UNIX?
A: Kick your boss’s ass, or, choose to work for a company who have decisions that you liked.






 Filed under:
Filed under: 
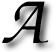 s some of you may have read, my site came under a large-scale
s some of you may have read, my site came under a large-scale 
 A long time ago I mentioned
A long time ago I mentioned  A week or so ago I notices a small swelling at the back of my neck. Such things are rather common, even among the healthy population, but they tend to draw my attention more than they should. This was not as worrying, however, as a similar tiny swelling near my bottom, which had me see my GP several months ago (in vain of course).
A week or so ago I notices a small swelling at the back of my neck. Such things are rather common, even among the healthy population, but they tend to draw my attention more than they should. This was not as worrying, however, as a similar tiny swelling near my bottom, which had me see my GP several months ago (in vain of course).
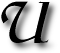 NDER the quiet exterior of
NDER the quiet exterior of 
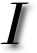 am never too aure as to how E-mail should be counted (if it can be counted at all). There is a certain amount of traffic that can be quantified when it comes to E-mail, but not all E-mails should be equally treated. Points to ponder:
am never too aure as to how E-mail should be counted (if it can be counted at all). There is a certain amount of traffic that can be quantified when it comes to E-mail, but not all E-mails should be equally treated. Points to ponder: