Think, Let the PDA Do the Rest
The post is addressed to readers who are not using a PDA yet. I would like to briefly describe the advantages of life management that is assisted by pocket-sized computing.
The acquisition of a first PDA, may it be a Palm, a Pocket PC or a Zaurus (there are many more), involves transformation of long-standing habits. It is an evolving process — an adaptation if you like — of what you have become accustomed to since childhood. Tasks are being managed and flagged by a machines rather than the brain. Then again, many of us use notes to manage and organise our lives, so the transition may be primarily a ‘digitisation’ of existing information management.
The key idea of using a PDA properly is this: program your tasks as you see fit, then obey in accordance with reminders from the PDA. It is as if the PDA commands its user what to do and when, relying on and benefiting from cyclic events and ensuring that nothing is ever forgotten or becomes a mental burden. The mind is left available to think and expand its horizons rather than record information. Let us face it, machines do a better job at registering without ever ‘forgetting’. It has been their very basic nature, since the early days of computers.

All your knowledge (and far more) in less than 1 gram
I can think of many advantages of using a PDA when compared with paper-based ‘life organisation’:
- Automatic archival
- Easy search
- Easier re-use of data
- Natural hierarchical abilities (not linear lists)
- Less clutter (e.g. no crossed-out items)
- Cyclic behaviour simplified, e.g. annual birthday notifications
- Vocal reminders/alarms
- Simple backups and duplication to prevent data loss
- Collaborative exchange of data, e.g. Wi-Fi, synchronisation, IR port
I could think of a few more, but these should be enough to convince you why the popular Hipster PDA (famous paper-based equivalent) can never be matched. It better fits technology paranoids.






 Filed under:
Filed under:  A long time ago I mentioned
A long time ago I mentioned 
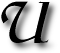 NDER the quiet exterior of
NDER the quiet exterior of 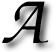 T this moment I am delivering a series of 4 one-to-one demos to prospective Ph.D. students. This occupies my morning and afternoon and I must admit that I quite enjoy it. I still remember the day when it was me whose ‘role’ was a student awaiting interviews and seeing some astounding demos. Once you grow to fit the very same shoes that you admired, it all seems somewhat worthless nonetheless. That, I suppose, is simply the way of life as the nature of progression. Below is a presentation that I primarily use to reflect on work that I do at present. I re-use this internal talk from earlier this year:
T this moment I am delivering a series of 4 one-to-one demos to prospective Ph.D. students. This occupies my morning and afternoon and I must admit that I quite enjoy it. I still remember the day when it was me whose ‘role’ was a student awaiting interviews and seeing some astounding demos. Once you grow to fit the very same shoes that you admired, it all seems somewhat worthless nonetheless. That, I suppose, is simply the way of life as the nature of progression. Below is a presentation that I primarily use to reflect on work that I do at present. I re-use this internal talk from earlier this year:
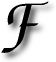 OR the sake of some short comical relief, use
OR the sake of some short comical relief, use 

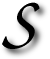 INCE I rarely post items about my personal life, I decided to make an exception today. On my very recent vacation, I taught myself a valuable lesson in bowling — a lesson that cost me an entire game that was filled with gutter balls and oddities. It was a game of exploration and experimentation.
INCE I rarely post items about my personal life, I decided to make an exception today. On my very recent vacation, I taught myself a valuable lesson in bowling — a lesson that cost me an entire game that was filled with gutter balls and oddities. It was a game of exploration and experimentation.
 EVIATING from the a development branch, thus staying away from the regular updates cycle, is a step which is bound to have its problems, e.g. security and missed out extensions. I am fully aware of these issues and I made mistakes in the past nonetheless, particularly with Web applications. I am rather confident and comfortable with my choices to extend applications, but one must remember the pitfalls, as well as the very few advantages.
EVIATING from the a development branch, thus staying away from the regular updates cycle, is a step which is bound to have its problems, e.g. security and missed out extensions. I am fully aware of these issues and I made mistakes in the past nonetheless, particularly with Web applications. I am rather confident and comfortable with my choices to extend applications, but one must remember the pitfalls, as well as the very few advantages.