KPilot Versus JPilot/GPilot
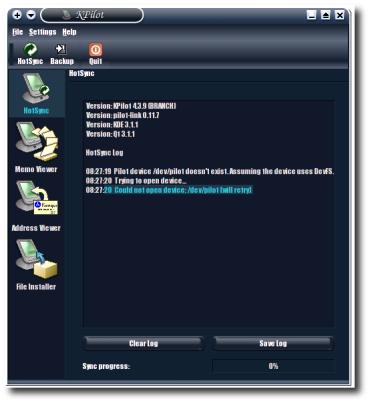
KPilot screenshot
version 4.3 on SuSE 8.2 (not the version reviewed below)
 INUX Palm synchronisation is a scarcely-explored territory to many. I currently own a Tungsten and I have 3 machines, all of which run Linux. In practice, I refuse to use my Palm for much beyond basic PIM, at least on a daily and thus realistic basis. Even MP3 playback capabilities have lost their appeal, so what I require is a rather rudimentary, but nonetheless user-friendly and reliable Palm-PC interaction suite.
INUX Palm synchronisation is a scarcely-explored territory to many. I currently own a Tungsten and I have 3 machines, all of which run Linux. In practice, I refuse to use my Palm for much beyond basic PIM, at least on a daily and thus realistic basis. Even MP3 playback capabilities have lost their appeal, so what I require is a rather rudimentary, but nonetheless user-friendly and reliable Palm-PC interaction suite.
Introduction and Disclaimer
I am fortunate to have had an opportunity to put both KPllot and JPilot on GNOME (gnome-pilot or gpilot) to the test. It seems as if they all trace back to a similar codebase, which includes pilot-link at the very core. My experience with the JPilot front-end is limited, so in my short review I will attempt to focus on default KDE and GNOME conduits — particularly the ones that come ‘out of the box’.
Admittedly, I only used GPilot for several weeks before looking into what KPilot (Version 4.5: “Baby”) had to offer, having glanced at it briefly last year. On equally-modern distributions, namely the GNOME-based Ubuntu Warty Warthog and the (largely) KDE-oriented SuSE 9.3 I have been putting Palm synchronisations to the test. Experimentation was a prolonged one and it covered some crash testing (hard-resets with data loss) and in-depth GUI exploration. This came after 3 years of using Palm Desktop under a Windows 98 laptop and a Windows 2000 desktop, I might add. All in all, there was good basis for inter-platform benchmarks, so critique should not have been a narrow-minded one.
Conclusions and Opinions
My first impression is that KPilot is more comprehensive than others, much like the entire desktop environment is resides in. I personally favour KDE although I use GNOME several times a week and almost every day. Overall, my opinion is not likely to have that ‘desktop environment bias’.
KPilot integrates rather well with its underlying/surrounding environment (e.g. mail client and calendaring software) whereas the GNOME equivalent is rather stripped-down and raw. The latter does what I require it to do and it even attempts to synchronise with Evolution (Outlook-type suite), which has been said to be slightly buggy. Nonetheless, it fails quite miserably at matching that ease-of-use of KDE’s equivalent. Firstly, setup in GNOME requires some hand-tweaking, at least in accordance with my own experience. This can end up consuming plenty of time. I also found the wizards in GNOME to be less helpful, more verbose, and more confusing.
Returning to KPilot, the front-end interface is a more natural one to its user. During synchronisation, all files are ordered with a sensible file structure under ./kde/share/apps/kpilot (or equivalents). gpilot, on the other hand, adheres to a flat hierarchy that provides little context, if any. Moreover, KPilot is largely intuitive, highly-customisable and comes with cleaner and apparently more comprehensive documentation.
Lastly, to those with strong sentiments of disagreement, I must clarify that everything was tested under Ubuntu and SuSE. All of the above observations can be attributed to distributions rather than the Palm conduits and packages. Nonetheless I would choose to go with KPilot as I presently do although I used gpilot at the start. It seems as though KPilot is simply more mature.
Your Palm and That Linux Migration
If you dread the day when you must synchronise your Palm with a new Linux box or a fresh installation, have a look at the very self-contained HOWTO.
Cited by: PalmAddict






 Filed under:
Filed under: 
 EHOLD the power of fibre-optics. Terabit connection, anyone?
EHOLD the power of fibre-optics. Terabit connection, anyone?
 HATEVER operating system we use, the idea of using remote terminals should not be foreign to us. These days, it is rather common to log on to a computer remotely and manage it from afar as if we were actually there.
HATEVER operating system we use, the idea of using remote terminals should not be foreign to us. These days, it is rather common to log on to a computer remotely and manage it from afar as if we were actually there.
 FTER
FTER 
 ICROSOFT are finally starting to
ICROSOFT are finally starting to 
 EMEBER the a popular phrase “Who is watching the watchers?”
EMEBER the a popular phrase “Who is watching the watchers?”